面试
https://www.managersclub.com/popular-interview-questions-for-engineering-managers/
https://igotanoffer.com/blogs/tech/engineering-manager-interviews#system-design
工作提升
https://newsletter.pragmaticengineer.com/p/templates-as-inspiration-for-engineering Resources for Engineering Managers and Software Engineers
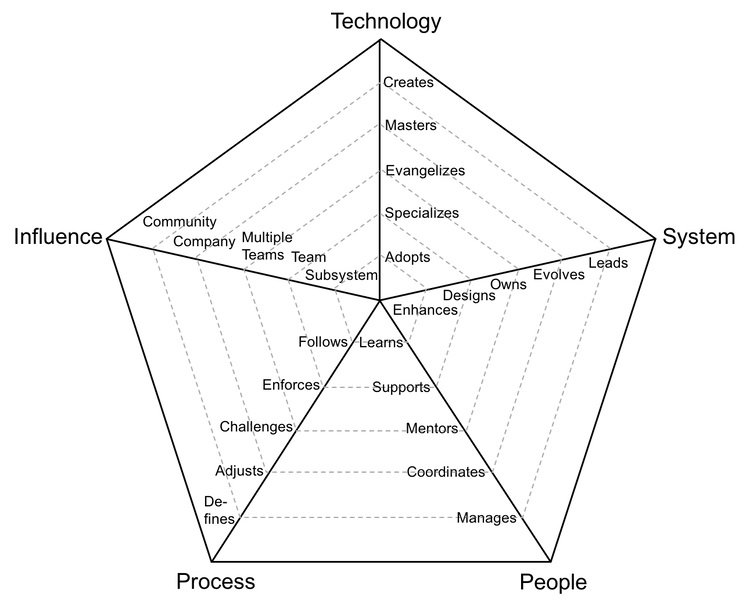
以公司为先,team次之,team member随后,个人最后
时间管理
https://www.quora.com/Does-a-software-manager-have-less-work-than-developers/answer/Jim-Plush
- Resource allocation - identifying upcoming projects and what resources can shift onto them
- Project prioritization - could be most important things or opportunity based things depending on who’s freeing up from projects/dealing with vacations, or other unexpected time off
- Interviewing and recruiting - a large part of a mangers job is recruiting and interviewing to help strengthen the team. This also includes salary and overall package negotiations
- Team Coach - scheduling and actively attending 1:1’s with team members to keep a pulse of the team and make sure people are happy with where their careers are and provide constructive criticism when needed.
- Team chef - ensuring during crunch times or in the case of a large, sustained outage the team is nourished
- PagerDuty scheduling - making sure there’s adequate coverage across the various parts of their services for production issues that may, no will, happen overnight.
- Technical oversight - making sure people are working towards shipping quality code vs research projects. Providing a sounding board for technical disagreements.
- Buffering the team from the chaos of upper level management who want to do a new feature every other day
- Managing up - providing roadmaps, status reports, production health dashboards to let executive teams understand where the team is
- Reviews and Promotions - a lot of time is spent in reviews and making sure people are getting promoted when they should, salary negotiation, perk negotiation, etc…
- Communication - as a manger you are the communication hub to relay what’s going on above you to your team and what’s happening with your team to your boss and above. Teams crave direction and understanding of where the company or org is headed, long term plans, short term plans, etc…
- Setting up or at least overseeing that you have the right processes in place for bug triage, code review workflow, ticketing/project management flows, roadmap/resource allocation methodologies.
- Understanding when to let someone go - Managers need to be able to design performance improvement plans and in times of failure, remove people from the team that may be underperforming or creating issues amongst the team. It’s like a band-aid, it should be done promptly so both parties can move on with their lives.
- Meeting fighter - making sure your team members aren’t spending all their days in meetings and actively working to either schedule meetings around clusters of times or trying to remove them entirely in favor of other mediums of communication.
- Customer liaison - working directly with customers for feedback or issues related to outages or expectations. Sometimes being brought into prospective sales to highlight technical details of your specific part of the organization.
- CSO - Chief Swag Officer, ensuring shirts,jackets,stickers,hoodies are delivered to everyone on the team, helping to budget for those items if the team expresses interest
- CLO - Chief Learning Officer, making sure your team has access to learning and educational budget and materials. Working with execs to establish budgets for conferences or other career advancement opportunities.
- CBO - Chief Budgeting Officer, making sure you have budgets for the resources you need for the upcoming quarter or year including headcount, software licenses, education material, swag, conferences, recruiting advertisement opportunities, food, snacks, gift card bonuses for small rewards, travel budget for remote teams.
- CCO - Chief Culture Officer, making sure that cultural norms are being upheld and helping to foster a positive culture. e.g. is there something happening in the org that isn’t to the standards or ideals. Backdoor promotions, salary imbalances, curbing naysayers, watching for burnout. A big part of culture is who gets hired, fired and promoted.
Questions
Do we need EM if we have Product Manager / Tech Lead? The question is like why we need CEO? CEO is the person truly understand the business, who can find the right people to work on the right thing and balance resources. It is not purely product and technology, people / culture / personal well-being are also important. CEO is thinking about how to make business excellent and sustainable, not only for now, but for long term.